CrossCurve Bridge Hack: $3M Stolen, Details
CRV/USDT
$50,765,363.71
$0.2581 / $0.2482
Change: $0.009900 (3.99%)
+0.0024%
Longs pay
Contents
Executive Summary
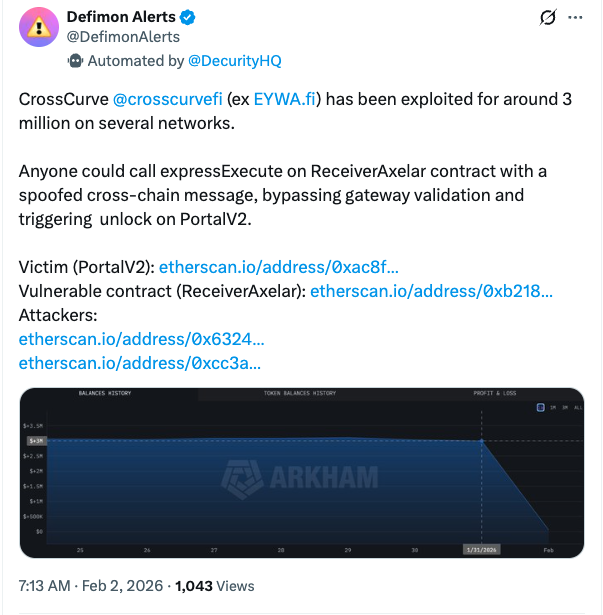
The CrossCurve protocol suffered approximately $3 million in losses due to a vulnerability in its cross-chain bridge. The attacker exploited the expressExecute function in the ReceiverAxelar contract to bypass the verification mechanism. All transactions were halted, and Curve Finance issued a warning. Discussions on bridge security have flared up across the market.
Expanded Original Content
The crypto protocol CrossCurve announced that its cross-chain bridge was attacked, with approximately $3 million stolen across multiple networks. The protocol announced on Sunday night on the X platform that a vulnerability in one of the smart contracts was exploited and requested that all interactions be stopped.
According to the Defimon Alerts account, one of CrossCurve's smart contracts allowed token unlocking by bypassing the verification mechanism with a fake message. Specifically, the expressExecute function in the ReceiverAxelar contract bypassed gateway verification and triggered the unlock process in PortalV2. Curve Finance recommended that users who voted for CrossCurve pools review their positions and remove their votes, emphasizing caution with third-party projects.
Breaking News Analysis
No additional breaking news so far (as of 01.02.2026). The incident is limited to the official announcement on X and Defimon Alerts. We are closely following developments; the protocol's forensic report and hacker tracking are expected. In similar incidents (e.g., Ronin, Wormhole), fund recoveries took weeks.
Technical Deep Dive
The attack stemmed from a critical flaw in the expressExecute function of the Axelar-based ReceiverAxelar contract. The transaction, which normally requires gateway verification, was bypassed with a fake message and triggered the PortalV2 unlock. This is a common risk in cross-chain relays: lack of message integrity verification.
| Detail | Description |
|---|---|
| Vulnerability | Gateway bypass in expressExecute |
| Affected Contracts | ReceiverAxelar, PortalV2 |
| Exploitation Method | Fake message with token unlock |
| Stolen Amount | ~3M USD, multiple chains |
Expert opinion: Relayer verification should be prioritized in audits. Similar vulns appear in over 20% of hacks on EVM chains (general industry data).
Related Coins Impact
Related coin not specified (N/A). However, Curve Finance (CRV) was directly affected; pool votes are at risk. Axelar (AXL) ecosystem is on alert. BTC as the main coin remains stable, with general market panic limited.
Market Context & Implications
Bridge hacks caused over 2B+ USD in losses between 2022-2025. The CrossCurve incident may pressure DeFi TVL by 1-2%. Curve users should withdraw liquidity. Regulators (SEC) may signal increased scrutiny.
| Bridge Hack Comparison | Amount | Date |
|---|---|---|
| Ronin | 625M$ | 2022 |
| Wormhole | 325M$ | 2022 |
| CrossCurve | 3M$ | 2026 |
Future Outlook & Key Levels to Watch
The protocol may publish an audit and bounty after the pause. Recovery fund possibility is high. Market: If BTC around 60K$ remains stable, impact will be limited. Watch: CRV 0.5$, AXL 1$ supports. Full forensic report expected within 48 hours.
Conclusion & Key Takeaways
- Stop all bridge interactions.
- Do not vote in third-party pools.
- Audits and verification are critical; functions like expressExecute are risky.
- Wallet security is a priority in DeFi.
CrossCurve can regain trust with quick intervention. Follow developments from COINOTAG.
Comments
Other Articles
Bitcoin Price Analysis: Will the Uptrend Continue?
2/21/2026
Ethereum 2.0 Update: How Will It Affect the Crypto Market?
2/20/2026
The Coming of Altcoin Season: Which Coins Will Stand Out?
2/19/2026
DeFi Protocols and Yield Farming Strategies
2/18/2026