Forensic Analysis Suggests Attacker Controlled ETH Whale Wallet Minutes After Creation
ETH/USDT
$15,764,184,570.61
$1,937.17 / $1,835.36
Change: $101.81 (5.55%)
-0.0004%
Shorts pay
Contents
A crypto attacker seized control of a whale’s multisig wallet just minutes after its creation on November 4, 2024, leading to losses exceeding $40 million. The incident involved a 1-of-1 configuration vulnerability, with funds laundered through Tornado Cash in staged batches over weeks.
-
Wallet Creation and Takeover: The multisig wallet was set up at 7:46 AM UTC but ownership transferred to the attacker six minutes later, suggesting premeditated compromise.
-
Attacker’s Strategy: Funds were drained gradually, with $12.6 million laundered via Tornado Cash and $25 million still held in the wallet.
-
Potential Losses: Forensic analysis from Hacken indicates total theft could surpass $40 million, including early signs from November 4 and ongoing leveraged positions.
Discover how a multisig wallet compromise drained over $40M from a crypto whale. Learn attack tactics, prevention tips, and AI’s role in exploits for secure investing today.
What is a Multisig Wallet Compromise in Crypto?
Multisig wallet compromise occurs when an attacker gains unauthorized control over a multi-signature cryptocurrency wallet, often through private key theft or configuration flaws, allowing fund drainage without victim awareness. In this case, a whale’s wallet was compromised minutes after creation on November 4, 2024, resulting in staged thefts totaling over $40 million. Blockchain forensics reveal the attacker used patient laundering tactics to evade detection.
How Did the Attacker Take Over the Wallet So Quickly?
The multisig wallet, designed for enhanced security by requiring multiple approvals, was ironically set as a 1-of-1 configuration, effectively functioning like a single-key wallet. Yehor Rudytsia, head of forensics at Hacken, analyzed on-chain data showing the wallet’s creation at 7:46 AM UTC, followed by ownership transfer to the attacker just six minutes later. This rapid handover suggests the attacker may have initiated the setup themselves, luring the victim into transferring funds before assuming control. Rudytsia noted, “Very likely the theft actor created this multisig and transferred funds there, then promptly swapped the owner to be himself.”
Blockchain security firm PeckShield first reported the incident on December 26, 2024, highlighting a private key compromise that led to $27.3 million drained from the wallet. However, Hacken’s deeper investigation pushed the estimated losses beyond $40 million, with initial theft signs traceable to November 4. The attacker retained about $2 million in liquid assets and maintained a leveraged long position on Aave, demonstrating sophisticated ongoing management.
Experts at Hacken, including decentralized application auditor Abdelfattah Ibrahim, pointed to common attack vectors such as malware on signing devices, phishing scams that prompt malicious approvals, or inadequate operational security like storing keys in plaintext. Ibrahim emphasized prevention: “Isolating signing devices as cold storage and verifying transactions beyond the user interface are essential to mitigate these risks.”
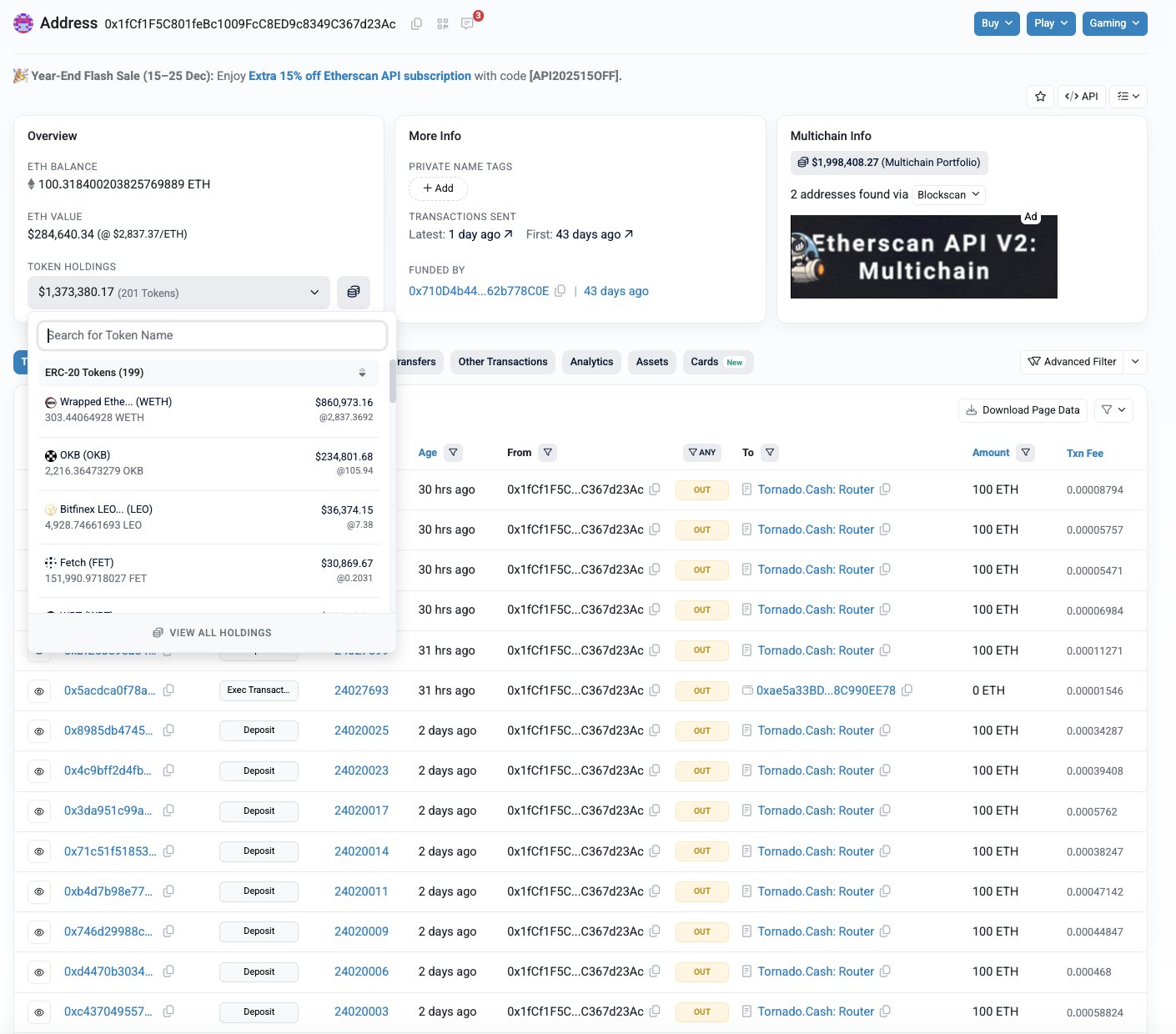
Attacker Plays the Long Game with Laundering
Following the takeover, the attacker adopted a deliberate, low-profile approach to extract value. Deposits into Tornado Cash began immediately on November 4 with 1,000 ETH, followed by smaller batches through mid-December, totaling about 4,100 ETH or $12.6 million laundered. This staggered method minimized on-chain footprints and delayed detection. Rudytsia from Hacken reported that approximately $25 million in assets remain in the compromised multisig, under the attacker’s control.
The 1-of-1 setup undermined the wallet’s security model, as only one signature was needed for transactions—a flaw Rudytsia described as “not a multisig conceptually.” This vulnerability highlights broader risks in crypto wallet management, where even advanced tools can fail due to misconfiguration.
AI Models Capable of Smart Contract Exploits
Amid rising wallet compromises, recent research underscores evolving threats from artificial intelligence. A study by Anthropic and the Machine Learning Alignment & Theory Scholars group demonstrated that leading AI models can autonomously develop profitable smart contract exploits. In tests, models like Anthropic’s Claude Opus 4.5 and OpenAI’s GPT-5 generated exploits valued at $4.6 million, proving the feasibility of AI-driven attacks using off-the-shelf technology.
Further experiments targeted nearly 2,850 newly launched smart contracts without known vulnerabilities. The AI models identified two zero-day flaws, creating exploits worth $3,694—slightly exceeding the $3,476 API costs to produce them. This capability signals a shift toward automated, intelligent cyber threats in the crypto space, where AI could accelerate exploits like the multisig compromise by analyzing code for weaknesses in real-time.
Such findings align with the patient tactics in this wallet incident, where manual sophistication met potential AI augmentation. As crypto infrastructure grows, integrating AI defenses will be crucial to counter these advanced persistent threats.
Frequently Asked Questions
What Are the Signs of a Multisig Wallet Compromise in Crypto Transactions?
Signs include unexpected ownership transfers shortly after wallet creation, staggered outflows to mixers like Tornado Cash, and retention of leveraged positions in DeFi protocols. In this case, forensic tools revealed a six-minute takeover and $40 million in phased drainages starting November 4, 2024, emphasizing the need for immediate on-chain monitoring.
How Can Crypto Users Prevent Wallet Takeovers Like This One?
To avoid multisig wallet compromises, use true multi-signature setups requiring multiple approvals, isolate devices for key management, and double-check transaction details offline. Experts recommend cold storage for signers and avoiding shared machines, as phishing and malware remain top risks in crypto security.
Key Takeaways
- Rapid Compromise Risk: Even newly created wallets face immediate threats if misconfigured, as seen in the six-minute ownership swap leading to over $40 million in losses.
- Patient Laundering Tactics: Attackers use batch deposits to Tornado Cash over weeks to obscure trails, with $12.6 million already processed and $25 million still at risk.
- AI’s Emerging Role: Advanced models like Claude and GPT-5 can exploit smart contracts profitably, urging enhanced verification and AI-resistant security measures in crypto.
Conclusion
This multisig wallet compromise exemplifies the sophisticated risks in crypto, where a seemingly secure 1-of-1 setup enabled $40 million in theft through quick takeover and gradual laundering. Insights from PeckShield and Hacken underscore the importance of robust configurations and vigilant monitoring to protect high-value holdings. As AI-driven exploits rise, staying informed and adopting layered defenses will safeguard the evolving crypto landscape—act now to audit your wallet security for peace of mind.
