Kaspersky Warns of Stealka Malware Targeting Crypto Wallets Through Game Mods
SFP/USDT
$1,776,884.87
$0.2705 / $0.2467
Change: $0.0238 (9.65%)
+0.0100%
Longs pay
Contents
Stealka malware is a new infostealer targeting cryptocurrency users by disguising itself as game mods and pirated software, stealing wallet data, passwords, and browser information to hijack accounts and install miners.
-
Stealka targets over 100 browsers and 80 crypto wallets like MetaMask and Trust Wallet.
-
It spreads via platforms like GitHub and fake professional websites mimicking game cheats.
-
Discovered in November by Kaspersky, it has affected Windows users through unofficial mods for games like Roblox.
Discover how Stealka malware threatens crypto security by posing as game mods. Learn essential tips to protect your wallets and avoid infostealers in 2025. Stay safe today!
What is Stealka Malware and How Does It Target Crypto Users?
Stealka malware is an advanced infostealer identified by cybersecurity experts at Kaspersky, designed to compromise Windows systems by masquerading as legitimate game modifications and cracked software. It infiltrates devices to extract sensitive data from browsers and cryptocurrency applications, enabling attackers to drain wallets and install unauthorized mining tools. First detected in November, this threat has rapidly evolved, exploiting user trust in unofficial downloads to access credentials for over 80 popular crypto platforms.
How Does Stealka Spread and What Data Does It Steal?
Stealka propagates through seemingly harmless files hosted on established repositories such as GitHub, SourceForge, and Google Sites, often bundled as cheats or mods for popular games like Roblox or cracks for tools like Microsoft Visio. According to Kaspersky researcher Artem Ushkov, attackers enhance their deception by employing sophisticated techniques, potentially including artificial intelligence, to craft entire fake websites that appear highly professional and convincing.
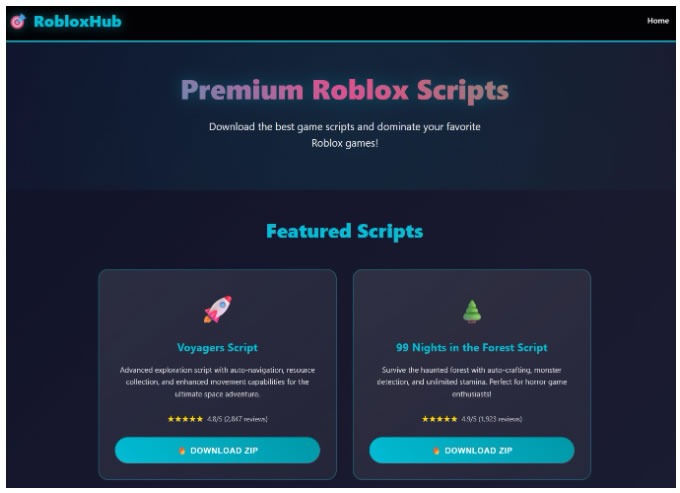
A fake website pretending to offer Roblox scripts, Source: Kaspersky
Once installed, Stealka boasts an extensive range of functions, focusing primarily on data from Chromium- and Gecko-based browsers, which encompass more than 100 options including Chrome, Firefox, Opera, Edge, Brave, and Yandex. It pilfers autofill details like login credentials, addresses, and payment information, while also targeting databases of 115 extensions related to crypto wallets, password managers, and two-factor authentication services.
Among the 80 cryptocurrency wallets at risk are well-known ones such as Binance, Coinbase, Crypto.com, SafePal, Trust Wallet, MetaMask, Ton, Phantom, Nexus, and Exodus. Beyond crypto assets, the malware extends its reach to messaging applications like Discord, Telegram, Unigram, Pidgin, and Tox, as well as email clients, gaming platforms, and VPN tools. This broad scope allows attackers to not only steal direct crypto holdings but also hijack accounts, deploy crypto miners, and perpetrate further fraud.
Kaspersky’s analysis, shared in their recent report, underscores the malware’s efficiency in evading basic detection, with infections leading to significant financial losses for victims. Ushkov emphasized that the malware’s modular design permits customization, making it adaptable to specific targets and harder to mitigate without comprehensive security measures.
To counter this threat, Kaspersky advises implementing robust antivirus solutions and dedicated password managers to minimize stored browser data. Users should steer clear of pirated software and unofficial game modifications, opting instead for verified sources to download content. Recent data from Cloudflare indicates that over 5% of global emails harbor malicious elements, with more than half featuring phishing links and a quarter of HTML attachments proven harmful, highlighting the pervasive nature of such risks in digital ecosystems.
Frequently Asked Questions
What Wallets Are Targeted by Stealka Malware?
Stealka specifically goes after 80 crypto wallets, including major ones like MetaMask, Trust Wallet, Binance, Coinbase, and Phantom. It accesses their extension settings and databases to extract private keys and credentials, allowing attackers to transfer funds without the user’s knowledge, as detailed in Kaspersky’s findings.
How Can I Protect Myself from Stealka-Like Threats in Crypto?
To safeguard against infostealers like Stealka, always download software and game mods from official sources, use antivirus software with real-time scanning, and store passwords in secure managers rather than browsers. Enabling two-factor authentication on all accounts adds an extra layer of defense against data theft.
Key Takeaways
- Stealka Disguises as Everyday Downloads: It hides in game cheats and software cracks on platforms like GitHub, tricking users into installation and exposing crypto data.
- Broad Browser and Wallet Coverage: Affects over 100 browsers and 80 wallets, stealing autofill info, credentials, and extension details for comprehensive account takeovers.
- Proactive Defense Measures: Avoid unofficial mods, deploy reliable antivirus, and use password managers to secure sensitive information and prevent financial losses.
Conclusion
In summary, Stealka malware represents a significant escalation in threats to crypto wallet security, leveraging deceptive tactics like fake game mods to infiltrate systems and siphon valuable data from browsers and applications. As cybersecurity firm Kaspersky highlights through its detailed investigation, vigilance remains key in an era where infostealers target digital assets with increasing sophistication. By adopting best practices such as verified downloads and layered protections, users can mitigate risks and continue engaging with cryptocurrency confidently, looking ahead to a more secure landscape in 2025.
Comments
Other Articles
Bitcoin Price Analysis: Will the Uptrend Continue?
2/28/2026
Ethereum 2.0 Update: How Will It Affect the Crypto Market?
2/27/2026
The Coming of Altcoin Season: Which Coins Will Stand Out?
2/26/2026
DeFi Protocols and Yield Farming Strategies
2/25/2026
