North Korean Hackers May Use Fake Zoom Calls to Steal Crypto, Experts Warn of $300M Losses
TON/USDT
$51,246,150.67
$1.306 / $1.224
Change: $0.0820 (6.70%)
-0.0132%
Shorts pay
Contents
The fake Zoom crypto scam involves North Korean hackers using deceptive video calls to install malware and steal over $300 million in cryptocurrency. Victims receive invites from trusted contacts via Telegram, leading to device infection during the call. Immediate actions include disconnecting from WiFi and transferring assets to secure wallets.
-
Scam initiation: Hackers impersonate known contacts on Telegram to invite victims to a fake Zoom meeting.
-
During the call, audio issues prompt a malicious patch download, infecting devices with malware.
-
Over $300 million stolen to date, according to security researcher Taylor Monahan, targeting passwords, private keys, and crypto holdings.
Discover the fake Zoom crypto scam by North Korean hackers stealing $300M+. Learn how it works and protect your assets today—transfer funds and secure devices now. (142 characters)
What is the fake Zoom crypto scam?
The fake Zoom crypto scam is a sophisticated phishing operation where cybercriminals, believed to be linked to North Korea, trick users into joining fraudulent video calls to deploy malware. This method has resulted in the theft of more than $300 million in cryptocurrency, as reported by cybersecurity experts. Victims often lose access to wallets, passwords, and sensitive data, highlighting the risks in digital communications within the crypto space.
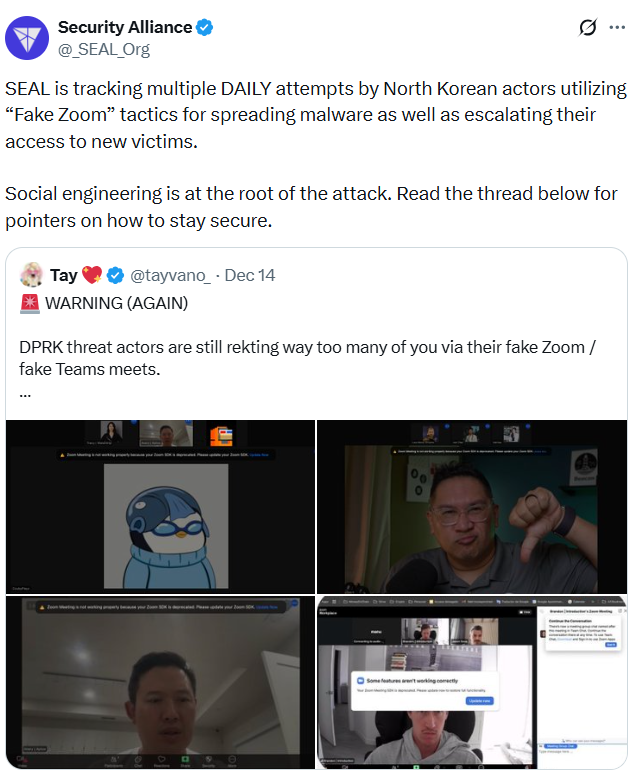
Source: Security Alliance
How do North Korean hackers execute the fake Zoom crypto scam?
Cybersecurity nonprofit Security Alliance (SEAL) has observed a surge in attempts by North Korean-affiliated hackers targeting crypto users through deceptive Zoom invitations. The scam begins with a seemingly innocuous message from a Telegram account mimicking a trusted acquaintance, building familiarity to lower defenses.
Security researcher Taylor Monahan explains that the hackers share a masked link disguised as a legitimate Zoom invite. Once joined, the call features pre-recorded videos of real individuals—sourced from prior hacks, public podcasts, or other accessible footage—rather than deepfakes, to maintain authenticity. As the session progresses, the perpetrators simulate technical glitches like audio failures and send a “patch” file via chat.
Opening this file installs malware that grants remote access to the victim’s device, enabling the theft of private keys, passwords, and cryptocurrency holdings. SEAL reports multiple such incidents daily, with Monahan noting the hackers often end the call casually, claiming to reschedule, to avoid immediate suspicion. “They’ll play it cool to prevent detection,” Monahan stated. “Your computer is already compromised—they will eventually take all your crypto, passwords, and more.”
This tactic exploits the trust in video conferencing tools, which have become integral to remote work and crypto community interactions. Data from SEAL indicates that infected devices can lead to broader compromises, including the hijacking of Telegram accounts to propagate the scam to contacts.
Frequently Asked Questions
What should you do if you’ve fallen for the fake Zoom crypto scam?
If you’ve clicked a suspicious link during a Zoom call, immediately disconnect from WiFi and power off the device to halt malware activity. Use a secure alternative device to transfer cryptocurrency to new wallets, update all passwords, enable two-factor authentication, and perform a full system wipe on the infected machine before reuse. Notify contacts promptly to prevent chain reactions.
How can you protect your Telegram account from North Korean hackers in crypto scams?
To safeguard your Telegram from exploitation in crypto scams like the fake Zoom attack, open the app on your phone, navigate to settings, review active devices, and terminate any unfamiliar sessions. Change your password immediately and enable or update multi-factor authentication. Security expert Taylor Monahan emphasizes alerting friends right away if compromised: “You need to tell everyone ASAP—you could hack your friends next.”
Source: Taylor Monahan
Key Takeaways
- Recognize red flags early: Unsolicited Zoom invites from Telegram contacts, even familiar ones, warrant verification through alternative channels before joining.
- Act swiftly on infection: Disconnecting from the network and isolating the device limits damage, allowing time to secure assets elsewhere.
- Prioritize account hygiene: Regularly audit Telegram sessions and enable MFA to block hackers from using your network to target others in the crypto community.
Conclusion
The fake Zoom crypto scam exemplifies the evolving threats from North Korean hackers in the cryptocurrency ecosystem, with losses exceeding $300 million underscoring the need for vigilance. By understanding how these operations exploit trust in tools like Zoom and Telegram, users can better protect their digital assets through proactive measures and swift responses. As cyber risks persist, staying informed and implementing robust security practices will be essential for safeguarding your crypto portfolio moving forward.
