Over 400 NPM Packages Potentially Compromised by Shai Hulud Malware, Affecting Ethereum ENS Tools
ENS/USDT
$12,687,172.06
$6.11 / $5.65
Change: $0.4600 (8.14%)
+0.0042%
Longs pay
Contents
The Shai Hulud malware has compromised over 400 NPM libraries, including at least 10 crypto-related packages mostly linked to Ethereum Name Service (ENS), in a major JavaScript supply-chain attack. This self-replicating threat steals credentials, potentially exposing wallet keys in developer environments, as identified by Aikido Security researcher Charlie Eriksen.
-
Over 400 NPM packages infected: Includes popular libraries with tens of thousands of weekly downloads, affecting developer tools across industries.
-
At least 10 crypto packages compromised: Primarily ENS-related, such as content-hash and address-encoder, used for human-readable Ethereum addresses.
-
Broader impact with 25,000 repositories: Cybersecurity firm Wiz reports over 25,000 affected repositories and 1,000 new ones every 30 minutes, urging immediate scans.
Discover the Shai Hulud NPM malware attack compromising crypto packages like ENS libraries. Learn affected tools, risks, and remediation steps to secure your development environment today.
What is the Shai Hulud Malware Attack on NPM Packages?
The Shai Hulud malware attack represents a significant JavaScript supply-chain compromise targeting NPM libraries, infecting over 400 packages as revealed by cybersecurity research. This self-replicating worm spreads autonomously through developer infrastructure, stealing credentials including potential cryptocurrency wallet keys. According to Charlie Eriksen of Aikido Security, the attack was validated to ensure no false positives, highlighting its scale in early September following a prior NPM incident that stole $50 million in crypto assets.
Which Crypto Packages Were Affected by the Shai Hulud Malware?
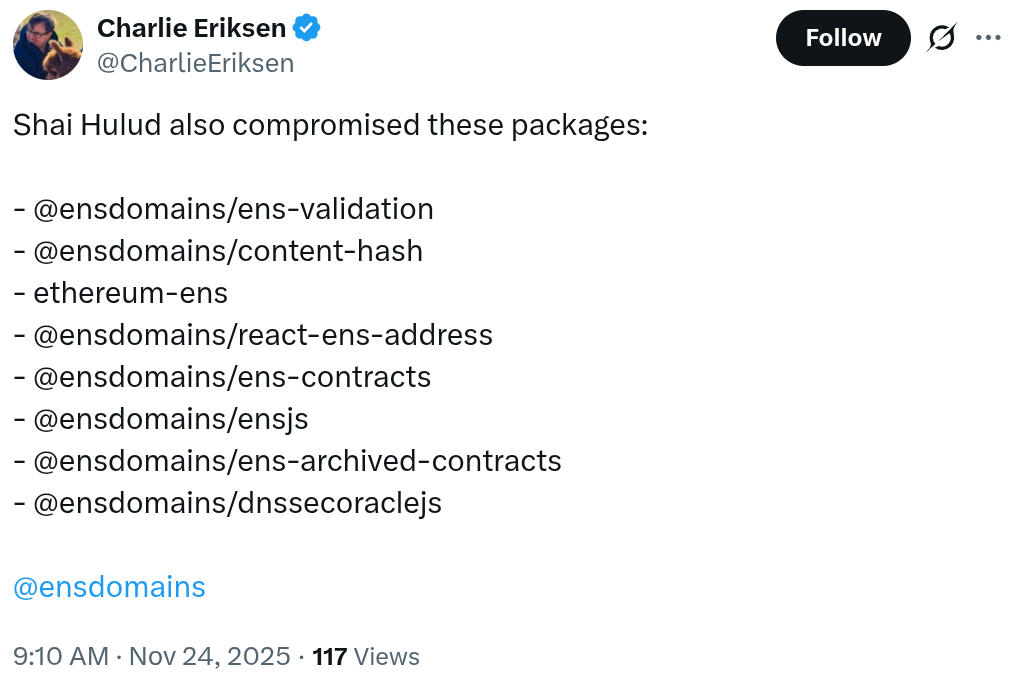
The Shai Hulud malware specifically impacted at least 10 cryptocurrency-related NPM packages, with nearly all connected to the Ethereum Name Service (ENS), a protocol for mapping human-readable names to Ethereum addresses. Key affected packages include content-hash, boasting nearly 36,000 weekly downloads and serving as a dependency for 91 other software packages; address-encoder, with over 37,500 weekly downloads; and ensjs, exceeding 30,000 weekly downloads. Additional ENS libraries hit are ens-validation (1,750 weekly downloads), ethereum-ens (12,650 weekly downloads), and ens-contracts (about 3,100 weekly downloads). One non-ENS crypto package, crypto-addr-codec, also fell victim, recording almost 35,000 downloads per week. These packages are integral to blockchain development, particularly for address handling and validation in Ethereum ecosystems. Eriksen directly notified the ENS team via social media, emphasizing the risk to widely used tools. Beyond crypto, the attack ensnared non-crypto packages, such as those from automation platform Zapier, one with over 40,000 weekly downloads. Eriksen noted in a post that some infected packages reach up to 70,000 downloads weekly, and another surpasses 1.5 million, underscoring the attack’s vast reach. “The scope of this new Shai Hulud attack is frankly massive; we’re still working through the queue to confirm it all,” Eriksen stated. Researchers at cybersecurity firm Wiz observed over 25,000 affected repositories across approximately 350 unique users, with 1,000 new repositories added consistently every 30 minutes in recent hours. They strongly recommend immediate investigation and remediation for any environments relying on NPM, as the malware operates as a general-purpose credential thief, targeting secrets like API keys or wallet information if present in infected setups. This contrasts with earlier NPM attacks focused solely on crypto theft; Shai Hulud’s autonomous spread amplifies its threat across diverse developer workflows. Amazon Web Services previously documented a related incident where the worm emerged just a week after the largest reported NPM crypto heist. The attack’s persistence highlights vulnerabilities in open-source supply chains, where unvetted dependencies can propagate malware rapidly. Developers are advised to audit their NPM usage, remove suspicious packages, and implement security scanning tools to mitigate exposure. While no direct asset theft from ENS users has been confirmed yet, the potential for credential compromise poses serious risks to Web3 projects relying on these libraries.
Source: Charlie Eriksen
Frequently Asked Questions
How Does the Shai Hulud Malware Spread in NPM Ecosystems?
The Shai Hulud malware spreads autonomously as a self-replicating worm within NPM libraries, infecting packages during installation or updates in developer environments. It targets JavaScript projects by embedding malicious code that propagates to dependent repositories, stealing credentials like environment variables or secrets without user interaction. Immediate package audits and dependency removal are essential to halt its spread, as validated by Aikido Security’s research.
What Should Developers Do If Their Crypto Projects Use Affected NPM Packages?
If your crypto projects rely on affected NPM packages like ENS libraries, start by scanning your codebase for infections using tools from firms like Aikido Security or Wiz. Remove compromised dependencies, such as content-hash or crypto-addr-codec, and regenerate any exposed credentials, including wallet keys. Monitor for unusual activity and update to verified versions to restore security in your Ethereum or blockchain development setup.
Key Takeaways
- Massive Scale of Infection: Over 400 NPM packages compromised, impacting 25,000 repositories and adding 1,000 more every 30 minutes, per Wiz research, affecting crypto and general developer tools alike.
- Crypto-Specific Risks: At least 10 packages tied to ENS, including high-download libraries like address-encoder with 37,500 weekly users, vulnerable to credential theft that could expose blockchain assets.
- Urgent Action Required: Developers must audit NPM dependencies immediately, remove infected packages, and implement ongoing security scans to prevent autonomous spread of Shai Hulud malware.
Conclusion
The Shai Hulud malware attack on NPM packages underscores the fragility of JavaScript supply chains, particularly for crypto packages like those in the Ethereum Name Service ecosystem. With hundreds of libraries infected and credentials at risk, including potential wallet keys, this incident demands heightened vigilance from developers and projects in the blockchain space. As cybersecurity threats evolve, staying proactive with audits and secure practices will be crucial to safeguarding digital assets and infrastructure moving forward.
Comments
Other Articles
Bitcoin Price Analysis: Will the Uptrend Continue?
2/28/2026
Ethereum 2.0 Update: How Will It Affect the Crypto Market?
2/27/2026
The Coming of Altcoin Season: Which Coins Will Stand Out?
2/26/2026
DeFi Protocols and Yield Farming Strategies
2/25/2026
